
Cybersecurity products
CYBERSECURITY, GOVERNANCE, RISK AND COMPLIANCE MANAGEMENT TOOLS
ESM CYBERSECURITY ™
Managing cybersecurity strategy and compliance is difficult without having the appropriate tools to do the job.
ESM cybersecurity enables IT leaders to manage their cybersecurity and compliance postures from a centralized dashboard, specially designed to formulate and create programs based on the most common security and compliance requirements and certifications, operationalize it, track progress, address gaps and communicate results.
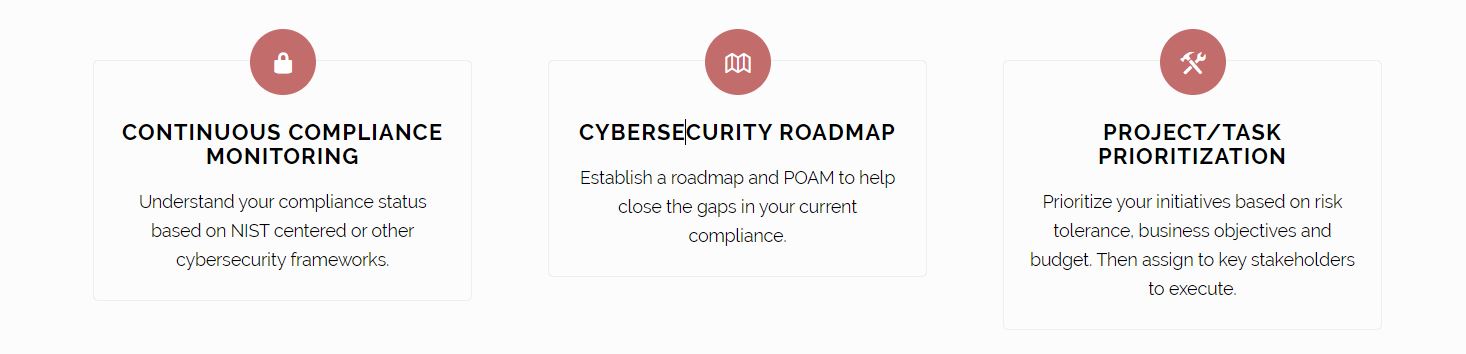
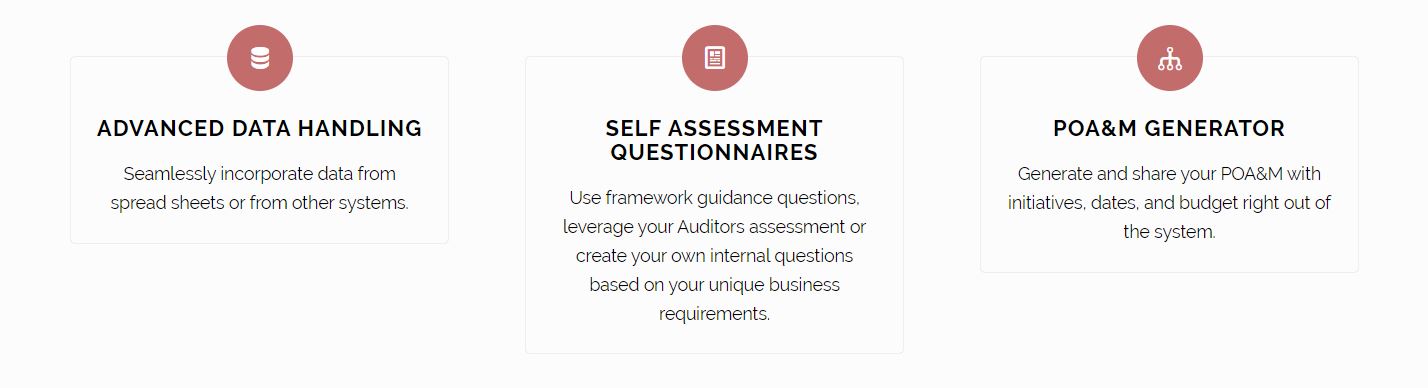
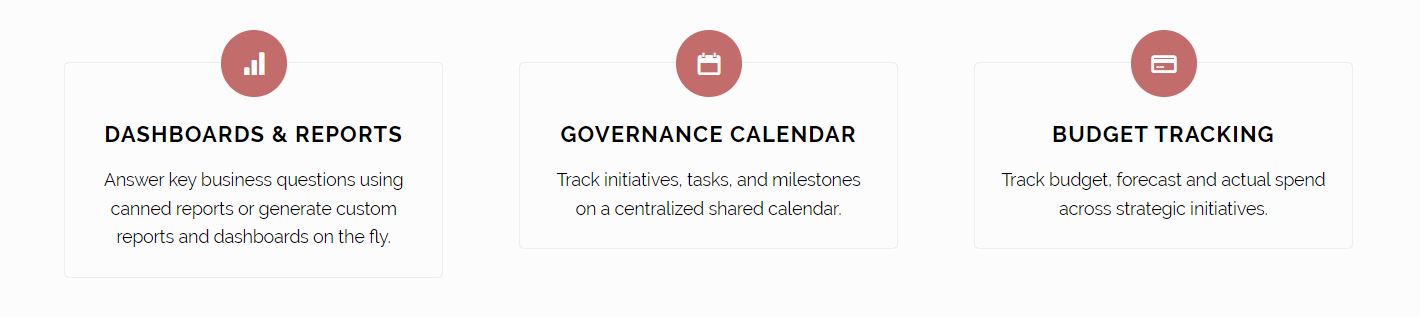
FEATURES & FUNCTIONALITY
GET CONTROL OF YOUR CYBER PROGRAM

QUANTUM RANDOM NUMBER GENERATOR (QRNG)
True Random numbers play an important role in data security to provide robust encryption. QRNG from addresses different data rates and standard interfaces to cater to applications.
Root of trust giving the perfect random numbers
Traditional RNGs like PRNG and TRNG use predictable inputs which are deterministic. These inputs have higher probability of repeating which creates predictability. Hence, making the entire system vulnerable.
QRNG does not rely on mathematical algorithms; it generates random numbers from a quantum source, making it suitable for all applications.
QUANTUM KEY DISTRIBUTION (QKD)
Quantum Key Distribution (QKD) product is a system that provides a solution to securely exchanging the encryption keys between two ends of a Symmetric Key Encryption system.
The basic principle is to exploit the principles of Quantum mechanics by utilizing encoded photons or “Qubits” to transmit the key from one end (Olli) to the other (Olivia) over a single fiber called the quantum channel. There are several ways or techniques to do this and all of them rely on the impossibility of anyone being able to tap or eavesdrop on the channel without getting detected.
ENTROPY AS A SERVICE (EAAS)
Random Keys as a service for Applications in Virtual Environments. EaaS solves the entropy starvation problem of systems, whether in a cloud, embedded systems or at the edge. EaaS provides the highest quality randomness and a secure method of providing the seeds for entropy starved systems or applications.
EaaS uses NIST architecture to establish a standard way of accepting keys.
POST-QUANTUM CRYPTOGRAPHY (PQC)
Achieve crypto agility and quantum readiness with one easy upgrade. PCQ is a post-quantum cryptographic algorithm developed by our partner with NIST PQC studies as reference. PQC is the next generation of protocol which will help replace todays RSA based systems with an improved quantum resistant transport layer. PQC is based on NIST selected mathematical functions, which are far harder to backtrack as compared to the prime factorization and elliptic curve functions on which the current PKI is based on.
FREE NETWORK SECURITY TOOLS
HAVEIBEENPWNED ™
Visit this website to check if your email address has been compromised in a data breach or other security incident.
When you register a domain with Haveibeenpwned you will receive an email alerting you if your domain has been compromised.
KEEPASS ™
KeePass is a free open-source password manager which helps you to manage passwords in a secure way. Passwords can be stored in one database and locked with a master key.
One only has to remember one single master key to unlock the whole database. Database files are encrypted using the best and most secure encryption algorithms currently known (AES-256, ChaCha20 and Twofish).
SNORT ™
Snort is an open-source Intrusion Prevention System (IPS). Snort IPS uses a series of rules that help define malicious network activity. It uses those rules to find packets that match against them and generates alerts for users.
Snort uses network-based intrusion detection/prevention systems (IDS/IPS) to perform real-time traffic analysis and packet logging on Internet Protocol (IP) networks. It can perform protocol analysis, content searching and matching. Snort can be configured in three main modes using: the sniffer, packet logger and network intrusion detection.
NIKTO2 ™
Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 6 700 potentially dangerous files and programs, outdated versions of over 1250 servers and version-specific problems on over 270 servers.
It also checks for server configuration items such as the presence of multiple index files, HTTP server options and will attempt to identify installed web servers and software. Scan items and plugins are frequently updated and can be automatically updated.
WIREGUARD ™
WireGuard® is a modern VPN that utilizes state-of-the-art cryptography. WireGuard is designed as a generic VPN for running on embedded interfaces and super computers and will fit for different circumstances.
Initially released for the Linux kernel, it is now cross-platform (Windows, macOS, BSD, iOS and Android) and widely deployable. While under continuous development, it is already regarded as one of the most secure VPN solutions in the industry.
